Security Tips
May 16, 2022


The stories of people losing everything to hackers and scammers are numerous and all too common in the crypto space. This is why the Blueshift team decided to educate its community and ensure it does not happen within the Blueshift ecosystem.
Both crypto veterans and crypto newbies need to adhere to these guidelines if they are to keep their crypto safe!
Some of these guidelines may be specific to the wide crypto ecosystem, and some might be specific to the usage of the Blueshift platform — while other guidelines might relate to both! Read carefully to make sure you do not put your hard-earned tokens and coins at risk!
The Guidelines
Only use verified fiat on and off ramps
Due to regulations or simply lack of knowledge of a newbie crypto user — some crypto users utilize very suspicious fiat on and off ramps that have exorbitant fees or simply steal all money transacted for the purchase of crypto. To those unacquainted with the term — a “fiat on ramp” is a service that offers the purchase of crypto via credit card, debit card, google or apple pay, and other means. A “fiat off ramp” is a service that offers to buy your crypto in exchange for fiat money. A “fiat on and off ramp” offers both.
Here is a list of fiat on ramps that the Blueshift team suggests for first time crypto users that are looking to acquire their first crypto:
Binance, OKex, FTX, Coinbase, Bybit, Bitfinex, Bitstamp, Bithumb and Kraken.
Don’t store your cryptocurrency on Centralized Exchanges
Just days ago, one of the largest Centralized Exchanges changed its policy stating that should they go bankrupt — the cryptocurrency of users that use their platform might be the one footing the bill for bankruptcy. In other words, if a Centralized Exchange goes bankrupt there is a chance you will lose all your cryptocurrency.
This same “principle” applies to hacking. If a centralized exchange gets hacked there is a chance you will lose your cryptocurrency without ever having it repaid back.
That is why it is best to store your cryptocurrency on an “on-chain”, or in other words, non-custodial wallet, such as MetaMask, Yoroi.
Double-check web domains and avoid phishing
Scammers often use something called “phishing” to steal cryptocurrency. Phishing is pretending to be something legitimate, when in fact it is a scam. The “pretending” part is usually done through websites that look identical to legitimate websites but are in full control of the scammers. For example, a scammer can create a website that looks exactly like the Binance Centralized Exchange which is the most used fiat on ramp in the world.
By using the scammer’s “Binance” users will unknowingly provide information to the scammer such as credit card info. The scammers will then charge them with fraudulent transactions or worse — steal the crypto from the “real Binance” by using the password and username provided by the user via the fake Binance.
The most common way to get crypto users onto fake versions of a legitimate service is through e-mails, Telegram, or Twitter messages or mobile phone SMS messages.
The scammer might go so far in its attack that you might receive an SMS message and the contact of the sender might say “Binance” even though it is not. Of course, such messages will be filled with great urgency warning you of the impending loss of all your crypto savings. The urgency is created to prevent people from thinking and double-checking.
To protect yourself from phishing use 2FA and a Browser-based password manager that will automatically recognize phished websites and will not fill in the password once a username is entered.
Keep your private keys — private
The so-called “private keys” or “seed phrases” are essentially the on-chain location and master password to your wallet which resides on the blockchain. Should someone find out the 12–25 word combination that represents the seed phrase of your wallet — this person can now access your account at any moment, without knowing the password usually required to sign a transaction.
That is why it is extremely important to store your seed phrase in a safe location!
Many consider your mobile phone or computer the least safe place to store your seed phrase — which makes writing down the seed phrase on paper a great alternative. In this case, however, the seed phrase is vulnerable in other ways. If you are physically storing your seed phrase by writing it on paper, or similar means, make sure to hide that paper extra well. When hiding the “paper wallet” avoid commonly used “secret” places like behind paintings. Be creative.
Use a hardware wallet
Many crypto users are adamant that a hardware wallet is the best security option to use for protection of cryptocurrencies. Even though it has been shown that hardware wallets also have vulnerabilities — the Blueshift team considers that at the current moment hardware wallets are indeed one of the best ways to store your cryptocurrency — safely.
Wallet recovery
Wallet recovery is one of the most common scams in the crypto space. A person pretending to be tech support or project team member will ask you to use a website (or even a google form) to “recover” your wallet for whatever reason they made up.
Do not do it.
If you do, your crypto is gone.
Be aware of different types of social engineering scams
There are so many types of social engineering scams, so let’s jump right into them.
For starters — there are no “multiplication” giveaways!
If you stumbled upon a video or live stream on youtube about sending any amount of cryptocurrency to a specific address — in order to receive back more tokens than you sent — don’t do it. This is a scam. Scammers might also contact you via Direct Message with this “great opportunity”. It is not an opportunity, it is a scam. You will not receive any tokens back.
There are many other types of scams perpetrated by Direct Messaging unknowledgeable crypto users such as offering technical support while posing as a representative of a project the unknowledgeable crypto user is following. Remember, technical support or team members of a project WILL NEVER DIRECT MESSAGE YOU FIRST, EVER! This holds true for Twitter comments as well! If you forget this simple rule, you might lose all your cryptocurrency.
Love scams are also common whereby mostly men pose as beautiful women and flirt with crypto holders. After some time the “beautiful woman” will ask you for cryptocurrency or money to “meet you” or some similar action. In this case “If it sounds too good to be true, it most likely is — too good to be true” — fits perfectly.
Avoid installing pirated software
Do not install pirated software onto a computer that you are using to transact cryptocurrency or use blockchain technology. Pirated software is often packed with malware such as keyloggers whereby it could log your seed phrase while you are creating a wallet. Malware can also take control of your computer and with the help of a keylogger that memorized your wallet password — simply steal all the crypto without possessing the seed phrase of the wallet.
This also applies to unknown browser extensions and mobile phone apps.
For the unacquainted — pirated software is software that usually has to be paid for, but the pirated version does not require that. It means the pirated version has been altered to avoid paying, which means it can also be altered in any way imaginable — to make it profitable for the pirate “editor”.
To avoid pirated software, simply google the name of the software and download the version of the software from its official distributor or creator.
Avoid using unknown wallets and dApps
The Crypto space is all about trying out new technology and being on the edge of things, however, if you are a crypto newbie — do not use unfamiliar wallets and dApps or you might lose everything.
If you are indeed a newbie — Metamask will most likely suffice for all your crypto needs outside of the Cardano ecosystem. If you wish to utilize the Cardano blockchain we suggest Nami, Eternl or Yoroi (or Daedalus if you love full nodes and being patient with technology).
Don’t interact with unknown tokens and NFTs in your wallet
Depending on which blockchain you use — it is possible to steal all your cryptocurrency, even if it is on a decentralized wallet — if you interact with a scam token that was sent to your wallet.
This is because EVM blockchains’ tokens are contracts and not native assets. In other words, if you “use” them by transacting them, you could be activating code hidden within the contract of the token.
If you notice a new token in your wallet that you have not purchased or acquired in a legit giveaway from a legit project — ignore it.
Avoid being the victim of sensitive information theft
There are many legit giveaways in the crypto space that are created as marketing campaigns intended to broaden the marketing reach of the giveaway originator.
Always keep in mind that in order to receive anything in the crypto space — one needs only the wallet address and nothing else. Never provide your name, address or other sensitive information for a giveaway, OR ANY OTHER REASON.
The only exclusion to this rule is passing the KYC process of legit services such as fiat on and off ramps or launchpads.
However, before filling in information during the KYC process — make absolutely sure that the service is legit and trustworthy. The best way to check for legitimacy is to ask one, two or even three veteran crypto users you personally know!
Double-check the address of a contract
If you are adding a token in your wallet, exchanging tokens over the counter (OTC) with an acquaintance, make sure to double check the contract of the token, or if the token is on Cardano — the policy ID of the token.
Policy ID can be checked via Cardano explorer, whilst the best way to check if a contract address is correct — is to write into coinmarketcap search bar the token ticker of a specific token, or the project name.
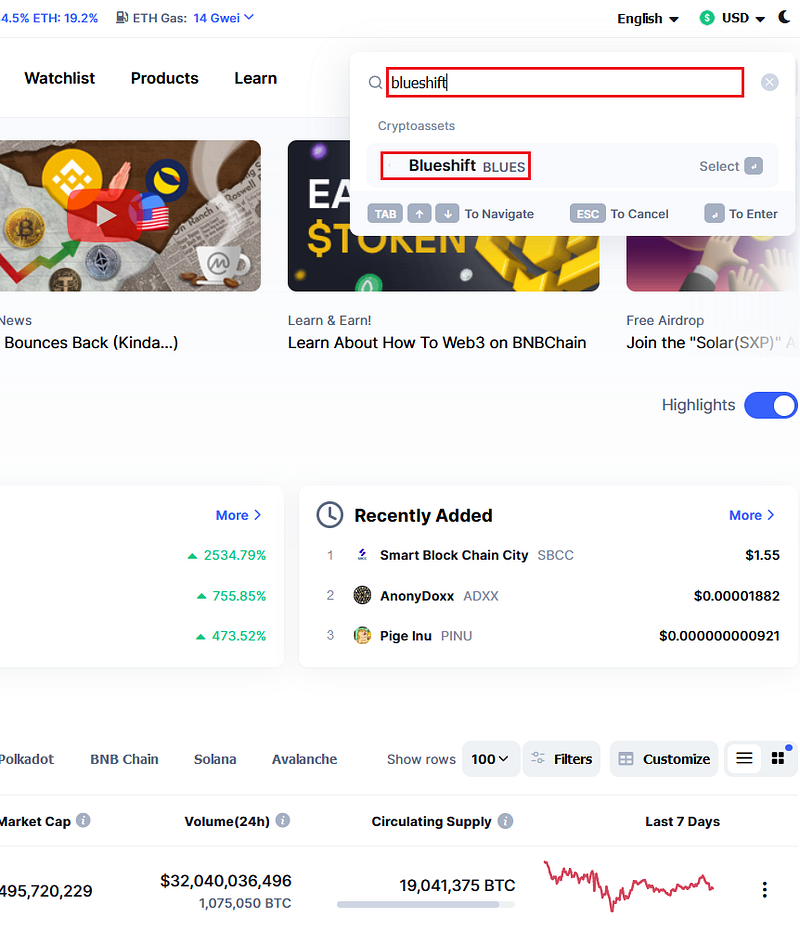
Click on the token ticker when it pops up.
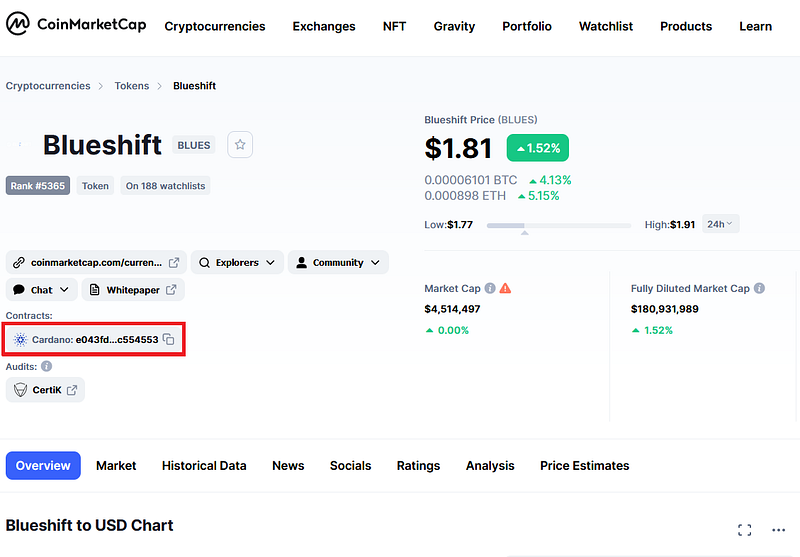
Now look at the “contract address” within the page that just opened — and compare it to the contract address of the token you are acquiring via unconventional means, or simply adding into your MetaMask.
This way you can ensure you are not in fact buying a copycat, as copycat tokens can have everything identical to the original token — including the logo, but the contract address cannot be faked.
Keep in mind — scammers can fake the beginning and the end of the EVM-based token contract to make them seem identical, so make sure to compare THE ENTIRE contract address — character by character.
Be patient
There are always big opportunities floating around in the crypto space. Scammers use this fact to push users into a scam by creating a false sense of urgency.
Never act in urgency, always take precautions, and always ask other people you trust for their opinion. It is better to miss a big opportunity than lose all your cryptocurrency.
New opportunities will come along the way!
Conclusion
If you stick to these guidelines it is almost certain that your funds will be SAFU!
Follow us on Twitter and Medium to learn more. If you want to become a part of the DeFi revolution swing by our Telegram Community and Discord!
Disclaimer:
The Blueshift team is not responsible for any losses incurred while adhering to these guidelines partially or fully, or not following these guidelines at all. Do Your Own Research. Protection of your tokens and coins is your responsibility.

